Overview of Essential Eight
Where did the Essential Eight come from, and who's it for?
Introduction
Sometimes, it’s helpful to contextualise what something isn’t. That is certainly the case with the Australian Signals Directorate’s Essential Eight Strategies to Mitigate Cyber Security Incidents.
The Essential Eight and its Maturity Model are often conflated with the Australian Government’s broader Protective Security Policy Framework (PSPF), which has its own Maturity Model.
So, to begin, let’s set the scene.
Contents
Where did the Essential Eight come from?
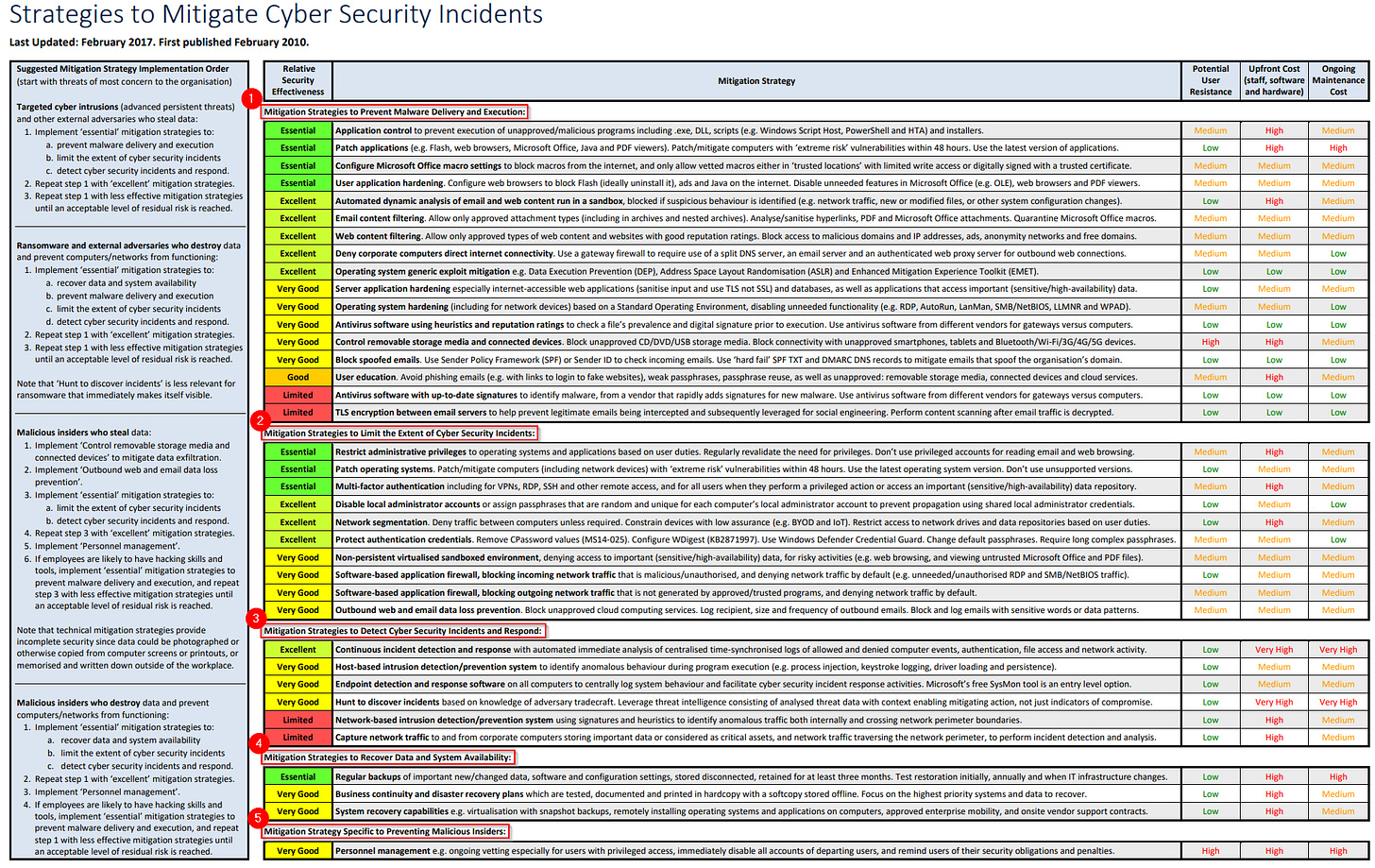
In February 2010, the Strategies to Mitigate Cyber Security Incidents was published to summarise the Information Security Manual. Seven years later, a revision added a degree of relative security effectiveness to these 37 strategies. Eight of these were marked Essential, thus giving rise to the Essential Eight.
Notably, the Essential Eight are not the Easy Eight. Nor is it the minimum needed for an effective cyber security posture. Instead, see it as a prioritisation. If you’re unsure where to start on a cyber security program of work, start with the Essential Eight.
Indeed, the PSPF is quite explicit about this. Policy 10: Safeguarding data from cyber threats states that entities must mitigate common cyber threats by implementing the Essential Eight and considering which of the remaining 29 strategies need to be implemented to achieve an acceptable level of residual risk.
The Essential Eight is not all that you need to do. Policy 10 creates a requirement for entities to consider what remaining mitigation strategies they need to achieve an acceptable level of residual risk.
Who’s it for?
The Essential Eight is not designed for all environments. It focuses on Microsoft Windows environments and may not be as relevant for other settings, such as IoT or Operational Technology.
Increasingly, government directives and legislative instruments are mandating the application of the Essential Eight as a risk management program.
The PSPF mandates it for most government entities at the Federal level
Some state governments have mandated it, including Victoria, Queensland, and New South Wales.
Entities designated as Critical Infrastructure (Security of Critical Infrastructure Act 2018)
Categorising the 37 strategies
The strategies are categorised into five types:
Preventing Malware delivery and execution.
Limiting the extent of Cyber Security Incidents.
Detecting Cyber Security Incidents and Responding.
Recovering data and system availability after a Cyber Security incident.
Preventing malicious insiders.
Source: cyber.gov.au
The strategies are also tagged against three further dimensions:
Potential User Resistance
Upfront cost
Ongoing maintenance cost
How these dimensions were baselined isn’t clear; presumably, it’s relative.
For the Essential Eight, there are:
Four prevention strategies.
Three limiting strategies.
One recovering strategy.
Where to start?
Logically, the advice is to follow a risk-based approach and start with strategies that mitigate the threats of most concern. This will look different for different organisations. The Strategies to Mitigate Cyber Security Incidents decompose this into four categories.
When implementing a strategy, first implement it for high-risk users and computers, such as those with access to important data and/or are exposed to untrustworthy internet content. Then, implement it for all other users and computers.
Targeted cyber intrusions and other external malicious actors who steal data.
Step 1
In this category, the first step is to implement the essential mitigation strategies that: a. prevent malware payload delivery and execution, b. limit the extent of cyber security incidents, and c. recover data and system availability.
Step 1 implementation order:
Application Control
Patch Applications
Configure Microsoft Office macro settings
User application hardening
Restrict administrative privileges
Patch operating systems
Multi-factor authentication
Regular backups
Step 2
Next, repeat the first step for the strategies with an effectiveness rating of ‘excellent’ in the detect, preventative, and limiting categories.
Step 2 implementation order:
Continuous incident detection and response
Automated dynamic analysis of email and web content run in a sandbox.
Email content filtering
Web content filtering
Deny corporate computers direct internet connectivity
Operating system generic exploit mitigation
Disable local administrator accounts
Network segmentation
Protect authentication credentials
Step 3
Lastly, consider what remaining strategies are required to achieve an acceptable level of residual risk1.
Ransomware and external malicious actors who destroy data
Step 1
For this category, the first step is to implement the Essential Eight that:
recover data and system availability,
prevent malware payload delivery and execution, an
limit the extent of cyber security incidents.
Step 1 implementation order:
Regular backups
Application Control
Patch Applications
Configure Microsoft Office macro settings
User application hardening
Restrict administrative privileges
Patch operating systems
Multi-factor authentication
Step 2
Next, repeat the first step for the strategies with an effectiveness rating of ‘excellent’ in the detecting, preventative, and limiting categories.
Step 2 implementation order:
Continuous incident detection and response
Automated dynamic analysis of email and web content run in a sandbox.
Email content filtering
Web content filtering
Deny corporate computers direct internet connectivity
Operating system generic exploit mitigation
Disable local administrator accounts
Network segmentation
Protect authentication credentials
Step 3
Lastly, consider what remaining strategies are required to achieve an acceptable level of residual risk.
Malicious insiders who steal data.
Steps 1 and 2
For this category, the first step is to implement data exfiltration by implementing the strategy ‘Control removable storage media and connected devices’. The second is to implement the limiting strategy: outbound web and email data loss prevention.
Step 1 and 2 implementation order:
Control removable storage media and connected devices.
Outbound web and email data loss prevention.
Step 3
Next is to implement the Essential Eight limiting strategies and those that allow detection and response.
Step 3 implementation order:
Restrict administrative privileges
Patch operating systems
Multi-factor authentication
Continuous incident detection and response
Step 4
Then, repeat the third step for strategies with an effective rating of excellent in the limiting category and implement the preventative strategy of Personnel Management.
Step 4 implementation order:
Disable local administrator accounts
Network segmentation
Protect authentication credentials
Personnel management
Step 5
Lastly, if employees are likely to have the technical cyber security capabilities, implement the remaining Essential Eight strategies to prevent malware delivery, then repeat step 3 with less effective mitigation strategies to achieve an acceptable level of residual risk.
Step 5 implementation order:
Application Control
Patch Applications
Configure Microsoft Office macro settings
User application hardening
Malicious insiders who destroy data and prevent systems functioning.
Step 1
For this category, the first step is to implement the Essential Eight that:
recover data and system availability, and
limit the extent of cyber security incidents.
Step 1 implementation order:
Regular backups
Restrict administrative privileges
Patch operating systems
Multi-factor authentication
Step 2
Next, repeat the first step for the strategies with an effectiveness rating of ‘excellent’ in the detecting and limiting categories.
Step 2 implementation order:
Continuous incident detection and response
Disable local administrator accounts
Network segmentation
Protect authentication credentials
Step 3
Next, implement the preventative strategy of Personnel Management. Again, if employees are likely to have the technical cyber security capabilities, implement the remaining Essential Eight strategies to prevent malware delivery. Then, repeat step 3 with less effective mitigation strategies to achieve an acceptable level of residual risk.
Step 3 implementation order:
Personnel Management
Application Control
Patch Applications
Configure Microsoft Office macro settings
User application hardening
Useful resources
Strategies to Mitigate Cyber Security Incidents | Cyber.gov.au
Policy 10: Safeguarding data from cyber threats | Protective Security Policy Framework
This is a requirement for entities covered by the Protective Security Policy Framework (see Policy 10: Safeguarding data from cyber threats, Requirement B.1.b)